Securely Access EC2 Instance Using Systems Manager Without SSH Keys
As a best practice we all know that our EC2 instances must not be directly exposed to the internet. So, we usually launch another instance (a bastion host / Jump box) in the public subnet or setup a VPN to have administrative access to our EC2 consoles. If your environment has both Windows and Linux Operating Systems for the EC2 instances, we will be forced to have a windows bastion host with terminal server license. Imagine if you have your application deployed in various regions, operational complexity and price overheads are something for given.
As a security best practice, we rather have no direct or indirect tunnels opened to our instances through any of the subnets in the VPC and all the public access for the EC2 instances happen through the NAT Gateway (AWS Managed or Unmanaged).
With this secure setup we can not only leverage the full features of AWS Systems Manager for managing AWS EC2 instances but also securely access them through the management console as well.
Please note that outbound internet connectivity is required to start accessing your instances from the AWS Management console.
Let us see what the requirements are and how do we make use of AWS Systems Manager to achieve this task.
Systems Manager IAM Permissions – Since the Systems Manager needs to have access to the EC2 instance the “AmazonSSMManagedInstanceCore” pre-configured policy needs to be added to the existing EC2 role or a new EC2 Role needs to be created.
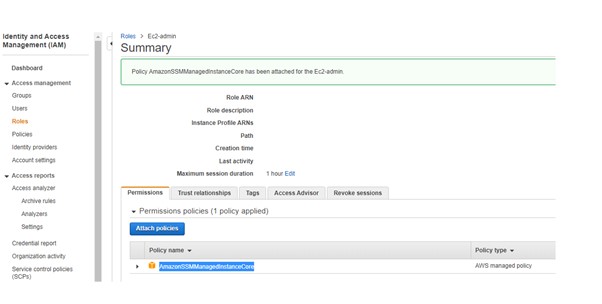
Attach this role to the Ec2 instances for the agent to work with the systems manager.
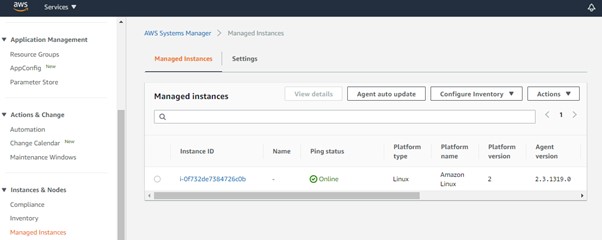
SSM agent is a software from Amazon which needs to be installed on the Ec2 machines. The job of this software is to update, manage and configure AWS resources. This agent acts as a mediator between the Ec2 instances and AWS Systems Manager Service.

By default, SSM agent is preinstalled if you are using Amazon Linux, Amazon Linux2, Ubuntu 16,18 & 20 Amazon machine images along with Windows Server 2016 & 2019. In case if you are using a Red Hat, SUSE Linux, or any other OS, you might want to manually install the agent. Here is an Amazon doc on how to manually install an SSM agent.
You also can install it during the launch process of the instances either in your autoscale launch configuration or when launching a new instance.
“#!/bin/bash cd /tmp curl https://s3.amazonaws.com/ec2-downoads-windows/SSMAgent/latest/linux_amd64/amazon-ssm-agent.rmp –o amazon-ssm-agent.rpm yum install -y amazon-ssm-agent.rpm” 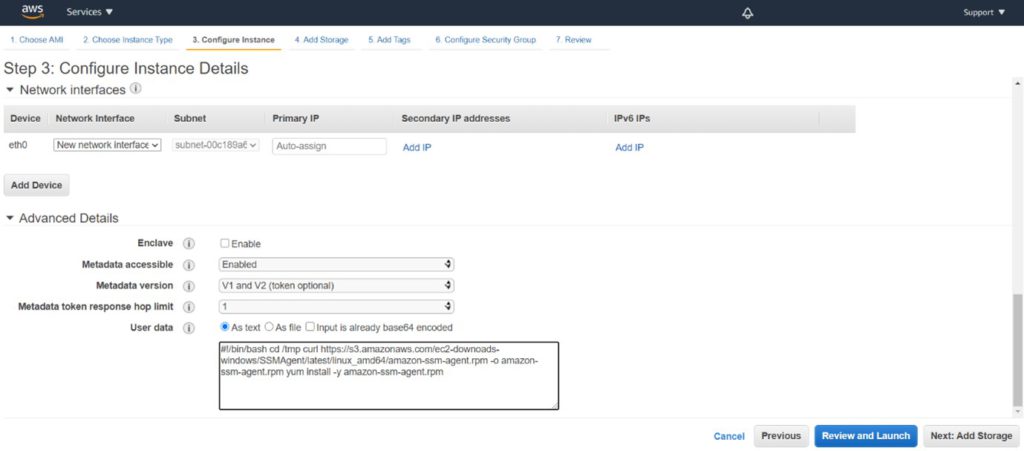
From the Ec2 dashboard, select the instance you want to connect to and select Session Manger.
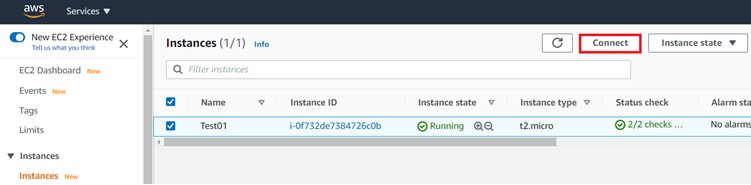
AWS Systems Manager Session Manager provides a secure and auditable instance management without the need to open inbound ports (like 22 or 3389) or use bastion hosts or manage any SSH related keys.
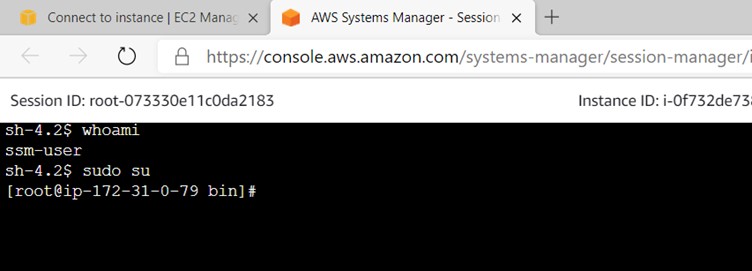
How does it help ?
- Since the SSH port is not opened, SSH brute force attack risks are eliminated completely as communication between instance and System Manager is through an encrypted tunnel.
- Bastion host is not required, and user is free from login to multiple systems before accessing the instances.
- The key sharing can be avoided and access to the instance can be limited using AWS IAM permissions.
- It provides an easy access to the EC2 instances, just like traditional virtualisation setup you can switch between the instances easily.
- Session Manager API can provide programmatic access and further integration with other services.
- Overall TCO is reduced and save on your monthly AWS billing.
HAVE QUESTIONS? FEEL FREE TO REACH OUT TO US HERE
Recent Posts
- How we revamped all GAIL Gas intranet applications and rolled out new applications.
- UX Design Trends: That Will Rule 2021
- TELANGANA STATE GOVERNMENT TRUSTS DATAEVOLVE FOR THEIR CLOUD
- APMDC BUILDS A FUTURE-READY ENTERPRISE WITH DATAEVOLVE
- AAROGYASRI BUILDS A FUTURE-READY INFRASTRUCTURE WITH DATAEVOLVE